The Go-based malware known as GobRAT targets Linux routers.
Yuma Masubuchi of JPCERT/CC gives information about a GobRAT malware attack that targeted Linux routers. A router with WEBUI that is accessible to the public is the attacker's initial target. After possibly exploiting script vulnerabilities, the attacker then launches GobRAT.
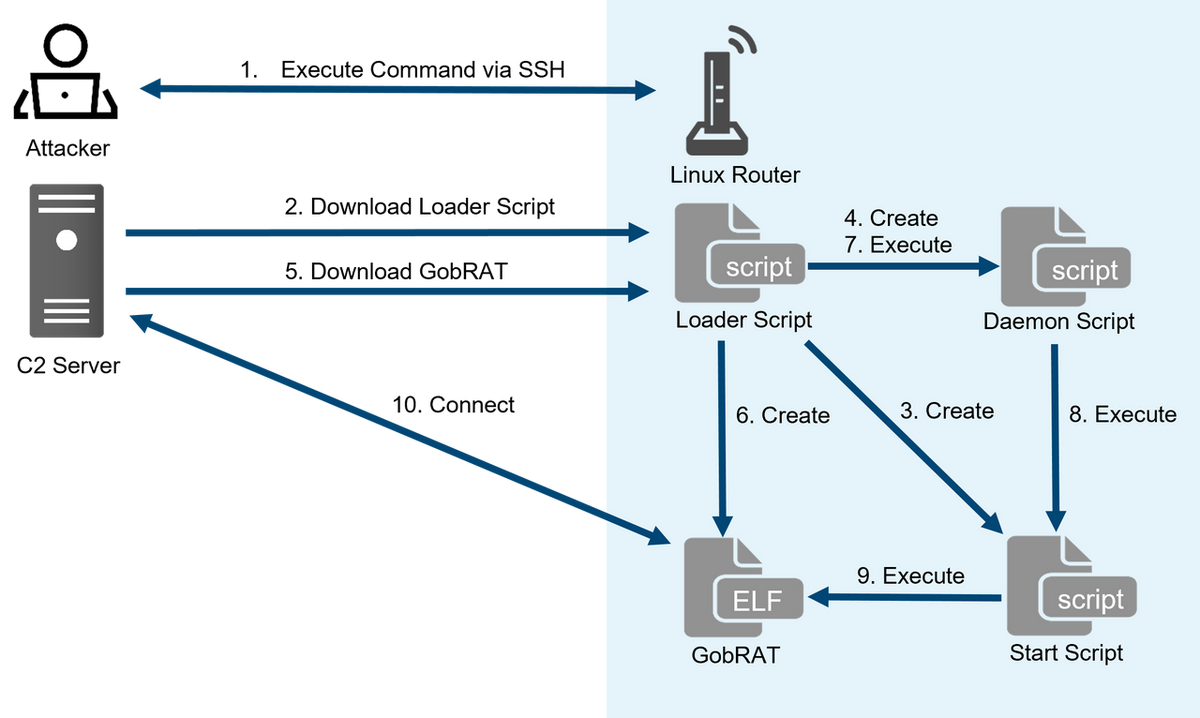
The attacker first targets a router with a public WEBUI, runs scripts that may exploit vulnerabilities, and then infects the GobRAT.
As a loader, Loader Script does tasks like creating different scripts and downloading GobRAT. The script has a hard-coded reference to the SSH public key, which is ostensibly utilised for the backdoor. Additionally, GobRAT lacks this feature since Loader Script uses crontab to register the Start Script's file location for persistence.
The following are some of Loader Script's features:
- Disable the Firewall feature
- For the architecture of the target machine, download GobRAT.
- Start Script should be made persistent.
- Make a Daemon Script and run it.
- Add an SSH public key to the authorized_keys file at /root/.ssh.
What's Your Reaction?

















